How to Secure SSH Access on CentOS 7
Date: 04-04-2020
Introduction:
SSH, also known as Secure Shell or Secure Socket Shell, is a network protocol that gives users, particularly system administrators, a secure way to access a computer over an unsecured network.
It provides several alternative options for strong authentication, and it protects the communications security and integrity with strong encryption.

1.Disable Root Logins:
For security concern, it is not recommended to use root user to login via SSH over a network.
To disable root login via SSH, update file /etc/ssh/sshd_config and restart SSH service as the following.
#vim /etc/ssh/sshd_config
PermitRootLogin no
#systemctl restart sshd
We will get a deny when trying SSH access with root user to the server.
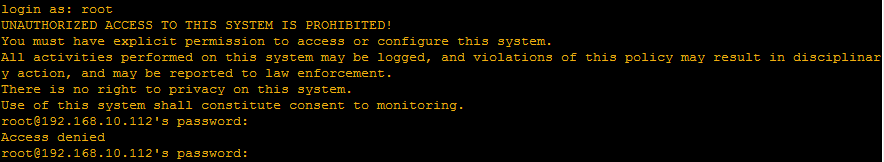
2.Limit User Logins:
By default, all valid users on the system are able to access the server. For security reason, we should limit to only certain users who really need to have SSH access to the server.
Add the parameter AllowUsers followed by a space-separated list of usernames to file /etc/ssh/sshd_config.
$sudo vim /etc/ssh/sshd_config
AllowUsers username1 username2
$sudo systemctl restart sshd
3.Disable Protocol 1:
Using protocol 1 of SSH is less secure. We should be disabled and always use protocol 2 only instead. Edit file /etc/ssh/sshd_config and restart SSH service as the following.
$sudo vim /etc/ssh/sshd_config
Protocol 2
$sudo systemctl restart sshd
4. Change Default Port:
Port 22 is the default SSH listens port for incoming connections. The hacker can constantly be scanning the server for port 22.
We can change the default SSH port, for example to port 2222 to eliminate this attacks as the following.
$sudo vim /etc/ssh/sshd_config
Port 2222
Now we need to check SELinux what ports sshd is allowed to listen by using the following command.
$sudo semanage port -l | grep ssh
ssh_port_t tcp 22
To allow sshd to listen on the new port 2223 we have to add a rule to SELinux and restart SSH service as the following.
$sudo semanage port -a -t ssh_port_t -p tcp 2223
$sudo systemctl restart sshd
5. Limit Access With Firewall:
For security enhancement, we should filter the connections with the firewall by adding a firewall rule in IPTables to limit access on the changed port 2222 to only an authorized IP address and Edit file /etc/sysconfig/iptables and restart IPTable service as the following.
$sudo vim /etc/sysconfig/iptables
-A INPUT -p tcp -m state –state NEW -m tcp -s 192.168.10.0/24 –dport 2222 -j ACCEPT
$sudo systemctl restart iptables
6.Limit Idle Timeout Interval:
In many cases, people stay away from their computers without locking the screens and SSH is still connected to the server and Edit file /etc/ssh/sshd_config as the following. The timeout interval is in seconds. So let set it to 300 seconds to have 5 minutes idle timeout.
$sudo vim /etc/ssh/sshd_config
ClientAliveInterval 300
ClientAliveCountMax 0
$sudo systemctl restart sshd
7. Limit Maximum Fail Authentication:
Limiting a maximum fail authentication with SSH is a good method to stop the password brute-forcing attacks. If a user inputs the password incorrectly for N-1 times of the limited N time, the SSH remote session will be disconnected and will have to reconnect again. In the below configuration, when the user incorrectly inputs the password for times, the remote session will be disconnected.
$sudo vim /etc/ssh/sshd_config
MaxAuthTries 5
$sudo systemctl restart sshd
8. Limit Listen Address:
The default configuration of SSH will listen on all available interfaces which should be limited. If there are multiple interfaces on the server configured with different IP addresses, it is always best to limit the user to login to the server using the management IP address only.
$sudo vim /etc/ssh/sshd_config
ListenAddress 192.168.1.100
$sudo systemctl restart sshd
9: Disable Empty Passwords Access:
The user account on the server might not have set a password or has an empty password. It is best to always disable these users connecting with a remote SSH server.
$sudo vim /etc/ssh/sshd_config
PermitEmptyPasswords no
$sudo systemctl restart sshd
10. Disable Host-Based Authentication:
Host-based authentication allows hosts to authenticate on behalf of all or some of the users using the public key.
$sudo vim /etc/ssh/sshd_config
HostbasedAuthentication no
$sudo systemctl restart sshd
11. Reduce Login Grace Time:
When we try to remote SSH a server, the default configuration will us 2 minutes to log in. If we do not do anything or cannot successfully login within 2 minutes, the SSH session will be disconnected. The default 2 minutes’ time to log in successfully is too much. we should consider reducing it to 1 minute instead.
$sudo vim /etc/ssh/sshd_config
LoginGraceTime 1m
$sudo systemctl restart sshd
12: Reduce Maximum Start Up Connection:
Reducing the maximum number of concurrent connections to the SSH daemon can be helpful against a brute-force attack. The setting of MaxStartups 4 tells the ssh server to allow only 4 users to attempt logging in at the same time.
$sudo vim /etc/ssh/sshd_config
MaxStartups 4
$sudo systemctl restart sshd
Conclusion:
It is a very helpful technique for securing your SSH server. This post covers almost all of the tasks that most users do for hardening an SSH server.