How to Create a Read-Only User for Kibana Dashboard (ELK Stack)
Introduction
In many organizations, it’s important to give users access to logs and dashboards without allowing them to make any changes. Kibana, the visualization tool for Elasticsearch in the ELK stack, allows you to create read-only users for this exact purpose. In this guide, we’ll walk through the simple steps to create a read-only user in Kibana who can view logs and dashboards but cannot edit or delete anything. This setup is perfect for developers, clients, or auditors who only need to monitor data.
Prerequisites
- Logs are already being ingested into Elasticsearch.
- Kibana index pattern is created (e.g.,
filebeat-*,logstash-*, etc.). - You are using X-Pack Security (enabled by default in the basic license from Elasticsearch 7.x+).
- You have access to the Kibana UI with an admin role.
Steps to Create a Read-Only User
1. Login to Kibana as Admin
Open your Kibana URL and log in using your admin credentials.
2. Create a Role for Read-Only Access
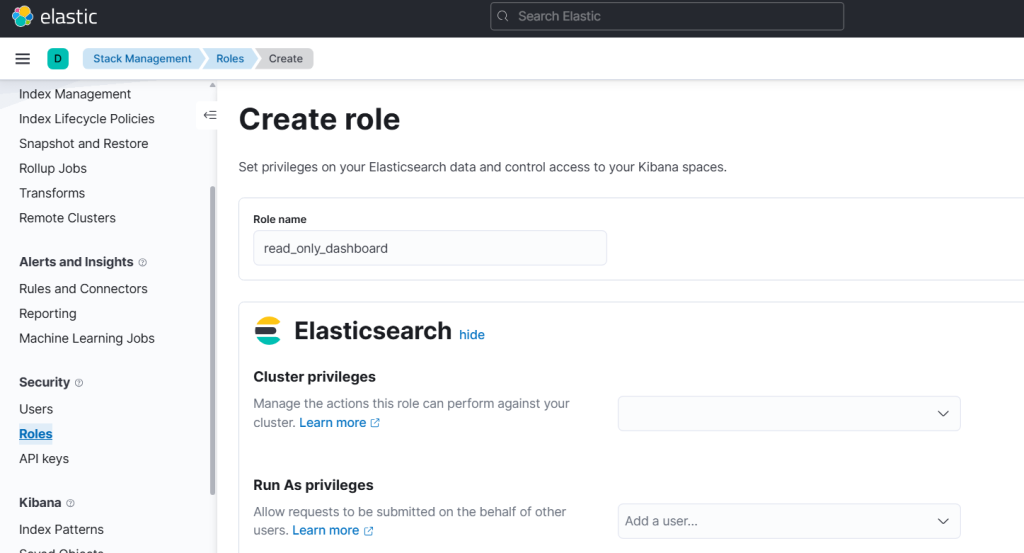
- Go to: Stack Management → Security → Roles
- Click Create Role
- Set a role name, for example:
read_only_dashboard
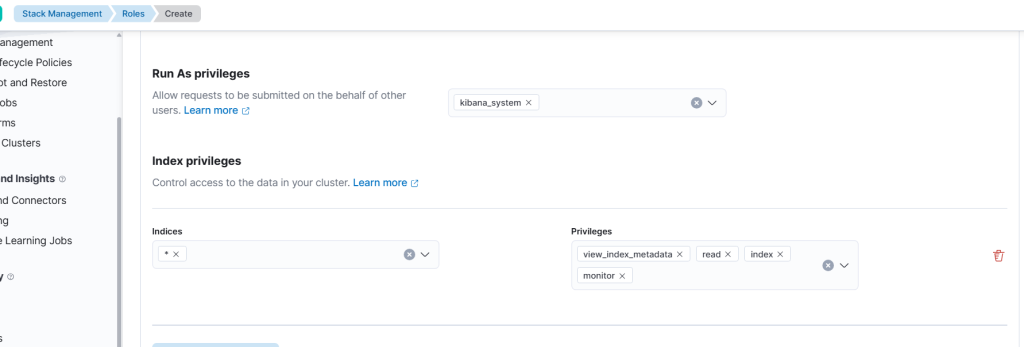
Elasticsearch Section:
- Run As privileges:
Add:kibana_system - Index privileges:
Indices:*
Privileges:read,monitor,view_index_metadata
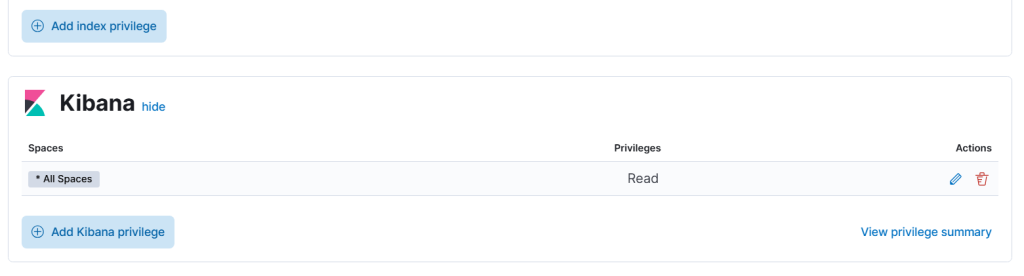
Kibana Section:
- Click Add space privilege
Choosedefault(or your specific space) - Set Privileges to:
Read
✅ This allows the user to view Discover, Dashboards, Visualize, and Lens, but not edit.
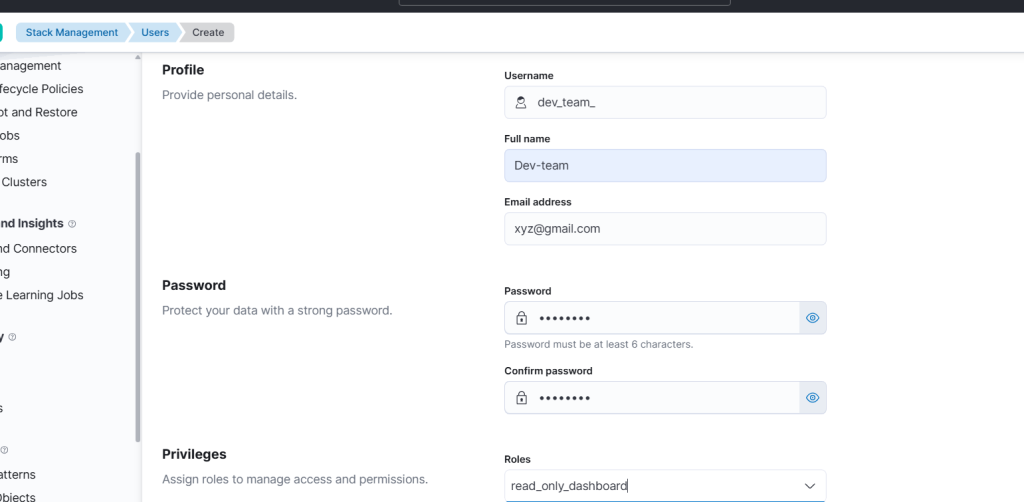
3. Create the Read-Only User
- Go to: Stack Management → Security → Users
- Click Create User
Fill in the user details:
Username:dev_team
Password:********
Full name:Kibana Read Only
Roles: Selectread_only_dashboard
4. Test the User
- Log out and log back in using the new
dev_team - Go to the Discover tab in Kibana
- You should be able to view logs and dashboards.
Conclusion
You’ve successfully created a read-only user in Kibana. This user can securely access log data and dashboards without any risk of modifying them. It’s a perfect solution for teams that need access to data insights but shouldn’t have admin control.
