How to Create and Use an Ansible Playbook
Introduction
In the modern DevOps landscape, automation is the backbone of efficient infrastructure management. Handling multiple servers manually over SSH can be tedious, error-prone, and time-consuming.
That’s where Ansible comes in—an open-source automation tool developed by Red Hat. It helps you configure servers, deploy applications, and manage systems seamlessly using simple YAML-based playbooks.
In this guide, we’ll walk you through—step-by-step—how to create, configure, and run your first Ansible playbook using a control node and managed nodes setup.
Prerequisites
Before getting started, make sure you have:
- Control Node—the main system where Ansible is installed and from which commands are run.
Example:Ubuntu 22.04 server - Managed Nodes—one or more remote servers to be configured using Ansible.
Example:2 Ubuntu 22.04 servers - SSH access—the control node must connect to each managed node using SSH.
- Python is installed on the managed nodes (Ansible uses it to run tasks).
Step 1: Install Ansible on the Control Node
First, log in to your control node and install Ansible:
sudo apt update
sudo apt install ansible -yVerify the installation:
ansible --versionStep 2: Set Up SSH Connectivity Between Nodes
To allow the control node to manage other servers, set up passwordless SSH authentication.
From the control node, run:
ssh-keygen -t rsaPress Enter to accept defaults (no passphrase required).
Manual Key Setup
On the control node:
cat /root/.ssh/id_rsa.pubCopy the full line (it starts with ssh-rsa or ssh-ed25519).
On the managed node:
sudo mkdir -p /home/ubuntu/.ssh
sudo nano /home/ubuntu/.ssh/authorized_keysPaste your public key inside the file.
Then fix permissions:
sudo chown -R ubuntu:ubuntu /home/ubuntu/.ssh
sudo chmod 700 /home/ubuntu/.ssh
sudo chmod 600 /home/ubuntu/.ssh/authorized_keysNow you can log in without a password:
ssh ubuntu@43.204.211.35Step 3: Configure the Inventory File
The inventory file tells Ansible which servers to manage.
By default, it’s located at /etc/ansible/hosts.
Open it:
sudo vi /etc/ansible/hostsAdd your managed node(s):
[webservers]
172.31.0.241 ansible_user=ubuntu ansible_ssh_private_key_file=/root/.ssh/id_rsa
172.31.14.164 ansible_user=ubuntu ansible_ssh_private_key_file=/root/.ssh/id_rsaRun:
ansible all -m pingIf everything is configured correctly, you’ll see:
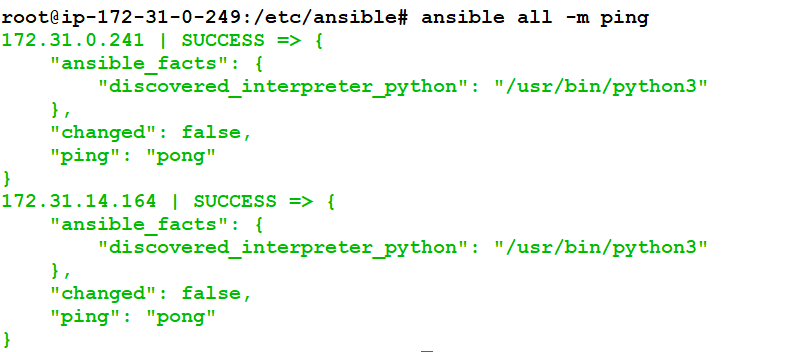
Step 4: Create a Directory for Your Playbooks
It’s best practice to keep playbooks organized in their own directory.
mkdir -p ~/ansible/playbooks
cd ~/ansible/playbooksStep 5: Create the Apache Setup Playbook
Create a new playbook file:
vi apache_setup.ymlPaste the following YAML code:
---
- name: Install and configure Apache web server
hosts: webservers
become: yes
tasks:
- name: Install Apache
apt:
name: apache2
state: present
update_cache: yes
- name: Start and enable Apache service
service:
name: apache2
state: started
enabled: yes
- name: Deploy custom index.html
copy:
dest: /var/www/html/index.html
content: "<h1>Hello from Ansible Apache Playbook!</h1>"Save and exit
Step 6: Run the Playbook
Run the playbook:
ansible-playbook -i /etc/ansible/hosts ~/ansible/playbooks/apache_setup.ymlAnsible will:
- Connect to all hosts under
[webservers] - Install Apache
- Enable and start the Apache service
- Deploy your
index.htmlfile
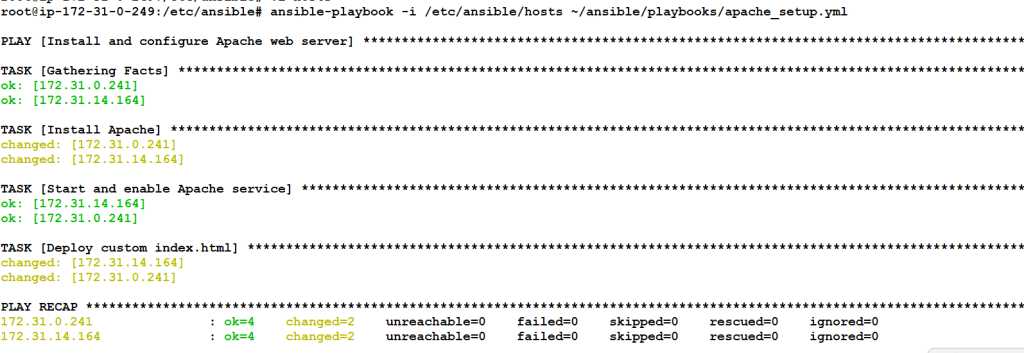
Step 7: Verify the Result
From your browser, visit:
http://<your-managed-node-IP>/You should see:
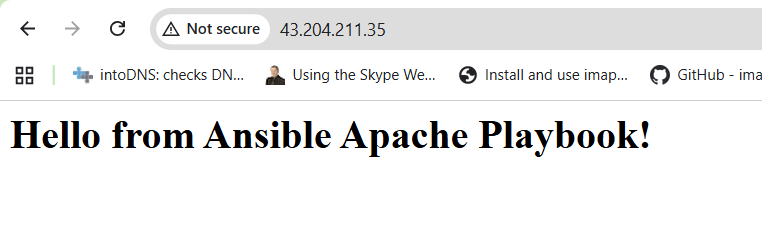
Step 8: Understanding Idempotency
A powerful feature of Ansible is idempotency —
You can run the same playbook multiple times, and Ansible will only make changes if something actually needs to be updated.
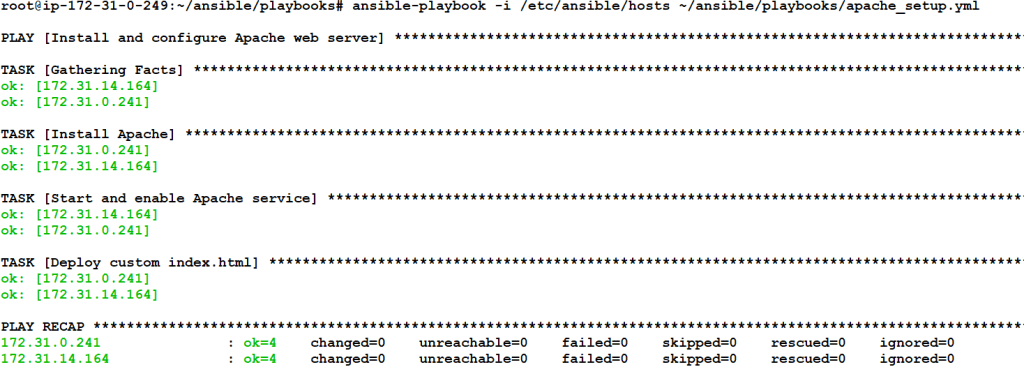
Try rerunning:
ansible-playbook -i /etc/ansible/hosts ~/ansible/playbooks/apache_setup.ymlYou’ll see most tasks marked as ok, meaning no unnecessary actions were performed.
Conclusion
Ansible makes automation simple, consistent, and scalable.
In this guide, we explored how to set up Ansible from scratch—from configuring SSH connectivity and defining an inventory to writing and executing your first playbook that installs and manages Apache on remote servers.
By using Ansible, you eliminate the need for repetitive manual tasks. Its idempotent nature ensures your servers always remain in the desired state, no matter how many times you run the same playbook.
Ansible is not just a tool—it’s a gateway to modern DevOps practices and Infrastructure as Code (IaC).
Keep experimenting, keep automating, and take the first step toward a fully automated infrastructure
