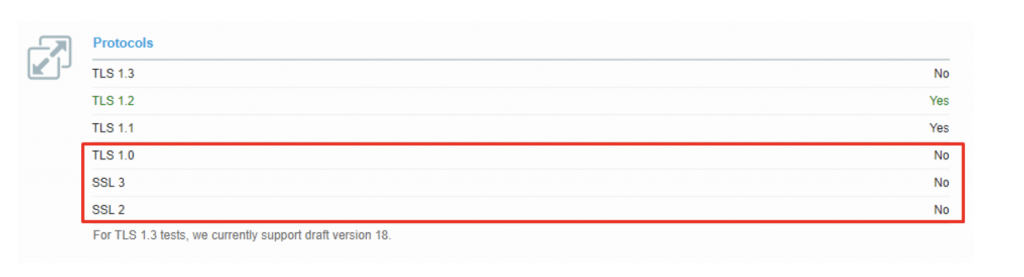
Hide server details and disable TLSV1.0 and TLSV1.1
Remove server name from Apache headers:-
It is essential to remove Apache server header to hide Apache server information and protect your website from malicious attackers. Here’s how to remove server name from Apache response header using htaccess. You can use it to hide the Apache version and server type in Ubuntu, CentOS.
- Open terminal and run the following command to open Apache main configuration file.
Centos:- vi /etc/httpd/conf/httpd.conf
Ubuntu:- vi /etc/apache2/apache2.conf - Turn off server signature. Add or Modify the below lines
ServerSignature Off
ServerTokens Prod
ServerSignature – appears at the bottom of server generated pages such as error pages, directory listings, etc
ServerTokens – decides what Apache will send back in response headers.
If you want to disable server signature in WordPress or turn off server signature in CPanel, then you will have to remove Apache server using .htaccess file, since you may not have access to Apache’s main configuration file.
Open CPanel, locate .htaccess file and edit it. Add the following 2 lines to .htaccess file
ServerSignature Off
ServerTokens Prod
3. Restart the Apache server with the below command.
systemctl restart apache2
Disable TLSV1.0 and TLSV1.1:-
All versions of the SSL/TLS protocol prior to TLS 1.2 are now deprecated and considered insecure. Many web server platforms still have TLS 1.0 and TLS 1.1 enabled by default. However, all modern web browsers are compatible with TLS 1.2. For this reason, it’s a good idea for website owners to check their server configuration to make sure that only current, secure versions of SSL/TLS are enabled and all others (including TLS 1.0, TLS 1.1, and SSL 3.0) are disabled.
You can also check for the SSL/TLS versions and ciphers supported by a website with the open-source nmap command-line tool:
nmap –script ssl-enum-ciphers -p <PORT> <DOMAIN NAME>
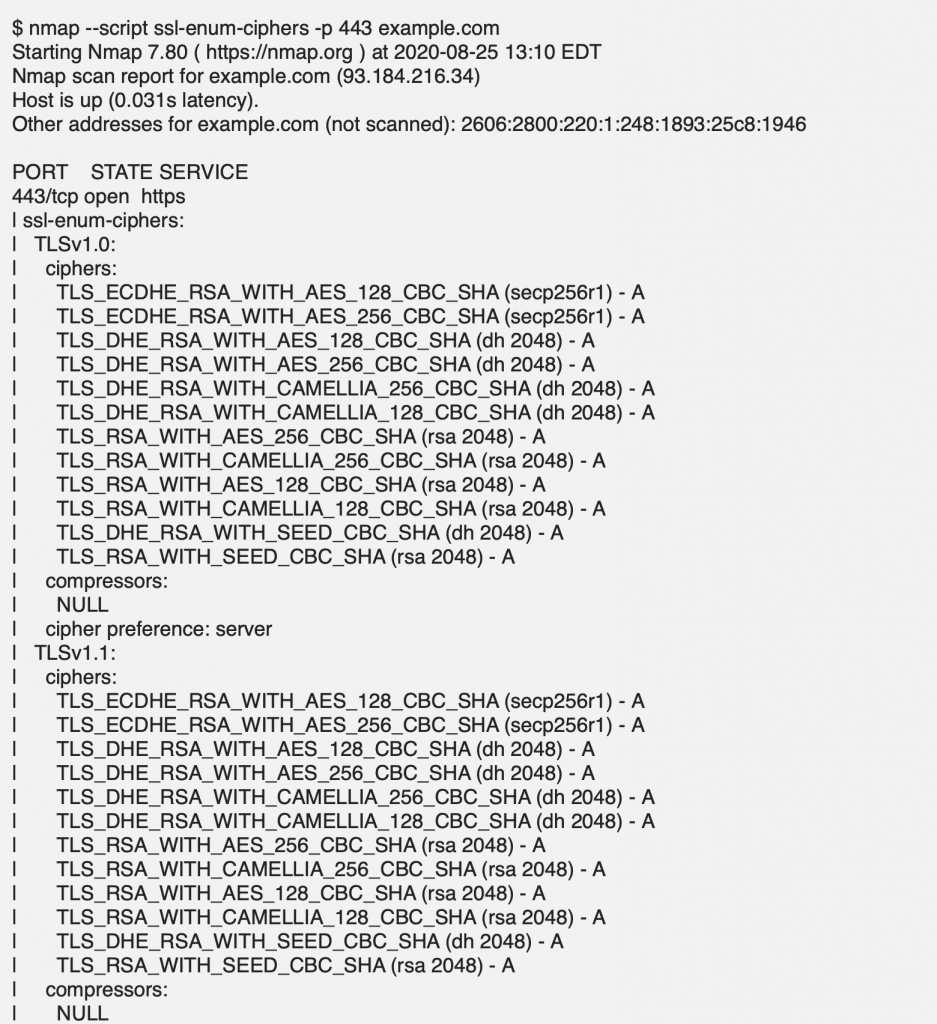
To disable TLS 1.0 and 1.1 in Apache, you will need to edit the configuration file containing the SSLProtocol directive for your website. This file may be located in different places depending on your platform, version, or other installation details. Some possible locations are:
Default Apache installation:- /usr/local/apache2/conf/extra/httpd-ssl.conf
Ubuntu/Debian:- /etc/apache2/mods-enabled/ssl.conf
macOS:- /private/etc/apache2/extra/httpd-ssl.conf
You can disable all obsolete versions of SSL/TLS supported by Apache by specifying them as follows:
SSLProtocol all -SSLv3 -TLSv1 -TLSv1.1
The configuration above enables TLS 1.2, as well as TLS 1.3 if it is available in your environment.
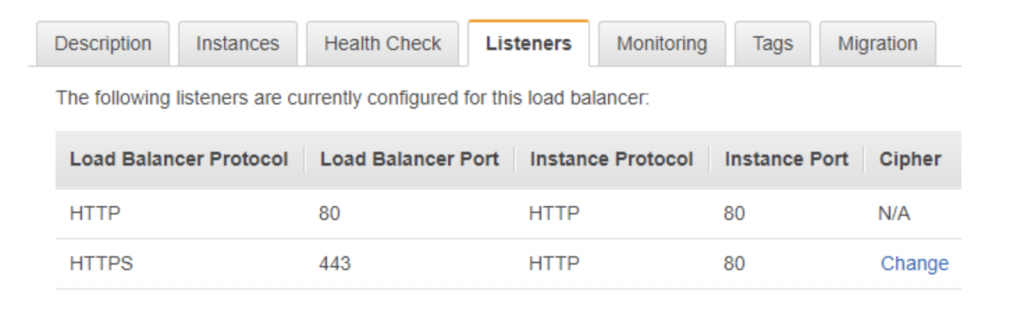
Disabling TLSV1.0 and TLSV1.1 at load-balancer level:-
1) Log into the AWS Console and navigate to the EC2 group. Within this group, click the Load Balancersoption under Load Balancing.

2) At the bottom of the screen, click the Listeners tab. You should see your HTTPS listener listed. Click the Change link under the Cipher column.
3) You will see a list of Predefined Security Policies in the window that just opened. Ensure you select at least the TLS 1.1 or higher policy. You will notice the selections in the window to the right changing, leaving both vulnerable protocols unchecked.
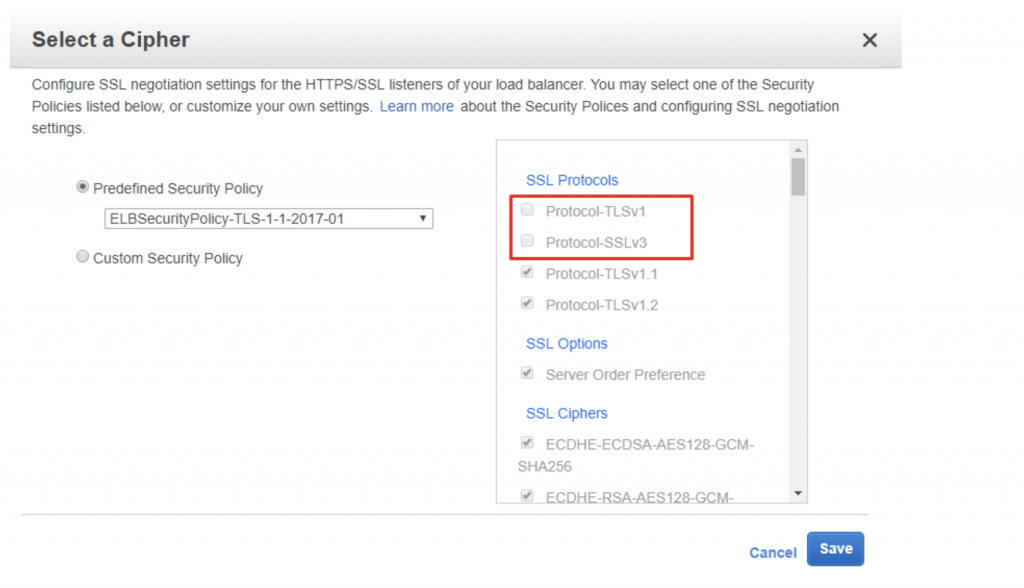
Finally, click the Save button to confirm the changes. You can make use of a service like Qualys to confirm your changes: