Things to know about Firewall cmd
Things to know about Firewall cmd
Date : 22-Oct-2018
firewall-cmd – Firewall Command Line Client tool. This is part of the firewalld application,which is installed by default.
Introduction:
Firewall-cmd is the command line client of the firewalld daemon (firewall management tool for Linux OS). It provides interface to manage runtime and permanent configuration.
The runtime configuration (non-permanent configuration) in firewalld is separated from the permanent configuration. This means that things can get changed in the runtime or permanent configuration.
It also provides an interfaces for services or applications to add iptables(ipv4),ip6tables(ipv6) and ebtables.
Note : ebtales – it is an application program used to setup and maintain tables of rules (inside Linux Kernel) that inspects Ethernet frame.
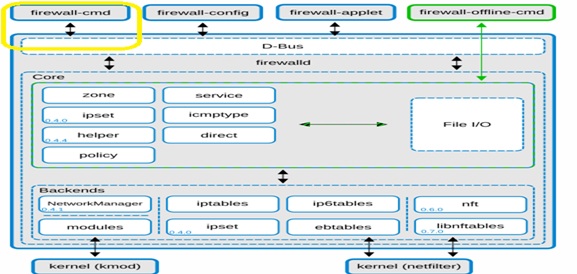
In this above fig,its clearly states that firewalld D-Bus will be act as primary way to apply the changes or create configuration.The interfaces used by the firewalld provided online tools such as firewallcmd ,firewall-config,firewall-applet.whereas,firewalld-offline-cmd bypass the firewalld D-bus directly to core layer with IO Handlers to alter or create configuration either permanent or runtime. But this one is not recommended because by this way we can only alter the permanent configuration and anyhow changes will be visible in firewall after about 5 minutes.
Assumption :
Practicing firewall commands in centos7 Linux Distribution.
1.Installation of firewalld
Following commands are for installing the firewalld in CentOS 7 Linux Distribution
#yum -y install firewalld
#systemctl enable firewalld
#systemctl restart firewalld
2.List of commands for firewall-cmd,
2.1 Basic Commands
#firewall-cmd --Version
#firewall-cmd --help
#firewall-cmd –state : check running or not
2.2 Firewalld is a zone based firewall, each zone is capable of configured to accept or deny some services with different level of security.
Zone can be associated with one or more interfaces.
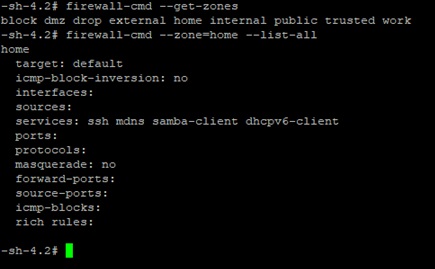
#firewall-cmd --get-zones
The above command shows what are zones available in the firewall system.But, if we need to know what services and ports available for them.
To view the services and ports for the particular zone, use the below command.
#firwall-cmd --zone=home --list-all
2.3 Firewall zone manipulation
The default zone is Public.How can we change the default zone (The default zone can be changed to any other zone by using following command),
# firewall-cmd –set-default= < choose your desired zone >
2.4 How to add service to the zone in firewall-cmd
Firstly service are preconfigured set of ports associated with protocol.
For example,
SSH service will include the port 22 TCP
Samba service will include the set of ports 139 & 145 TCP and 137 & 138 UDP
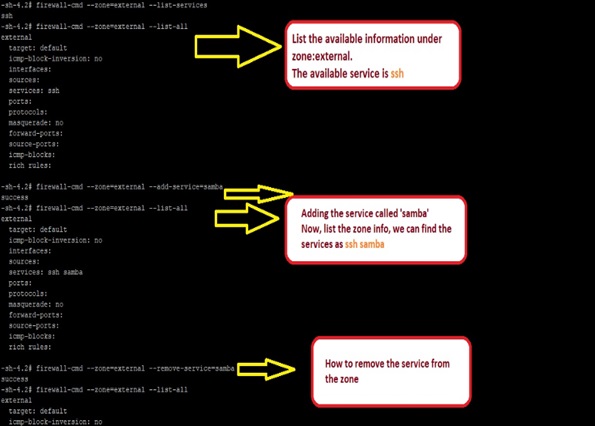
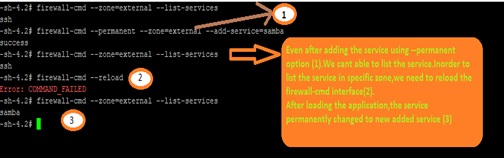
Now we are adding/removing services to the zone and verifying it using following commands,
The above command is as runtime configuration (non-permanent).If we reload the firewall system,this changes maynot be available in the list. Lets check it,
To make it persistent modification to a zone, we need to add –permanent option in the command.
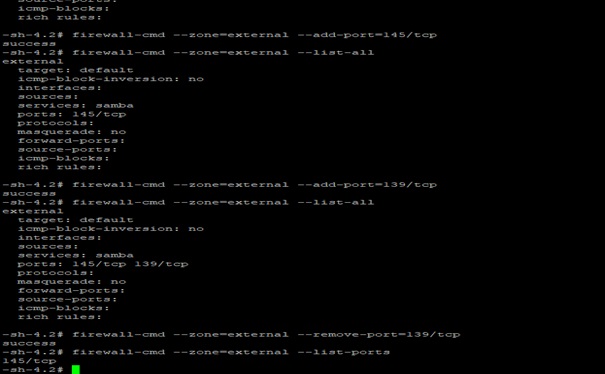
2.5 How to add ports to the zone in firewall-cmd
Following the same steps as like service for ports (just replace service as port and its identity)
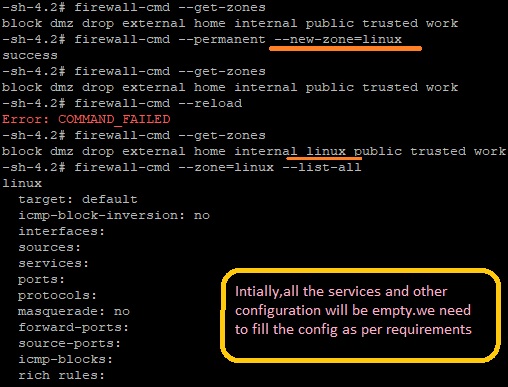
2.6 How to add zones to the firewall-cmd
In above content we seen only how to alter the existing zone.Now lets see about how to create the zone.
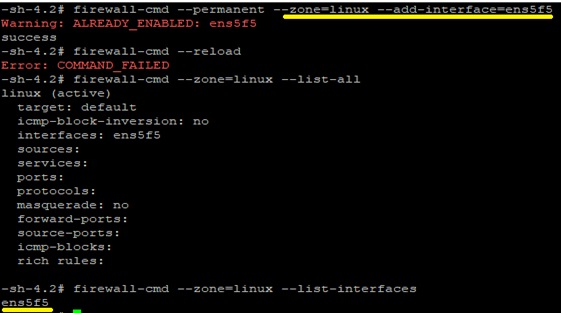
2.7 How to associate a zone with interface
Creating a zone in the firewall system is first step.Now, we want to use the new created zone , associating with the ens5f5 ethernet interface.
2.8 How to delete the existing zones,
Note : Important contents need to know as follows,
2.9 RICH rules
In certain situations we need to create more complex rules as not allowing some ports and some services in particular zone.
The rule comprehended into two parts:
1st : Specifying the condition which might be applicable
2nd : Execution, if rule 1 satisfied the following action to be executed either accept or drop or reject.
Scenario,Lets say for example if I need to block the traffic from ip 192.168.1.0 in local network.
The rich rule will be,
#firewall-cmd –zone=external –add-rich-rule=”rule” \family=”ipv4” \ source address =192.168.1.0 \ service name =ssh\reject\
2.10 Panic Mode
The panic mode is a mode that could be used only in situations when there is serious problem in the network environment.When this connection is enabled,all other exiting connections are discarded and all incoming/outgoing packets are dropped.
#firewall-cmd – -panic-on %%% to enable this mode
#firewall-cmd – -panic-off %%% to disable this mode
#firewall-cmd – -query-panic %%% to query panic mode status
Note : FYI, this mode only works in the run time configuration and cannot be used with the – – permanent.
Hope this post will be useful for basic understanding of firewall-cmd in centos 7 distribution. Please leave a reply, for any suggestions/queries which will be useful for us to serve in a better way.